How to remove EByte Locker Ransomware and decrypt .EByteLocker files
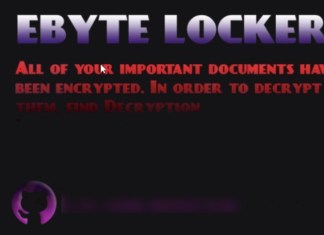
EByte Locker Ransomware is a sophisticated type of malicious software that falls under the ransomware category. This malware is notably derived from the Prince ransomware family, highlighting its robust encryption capabilities. Once this ransomware infiltrates a system, it targets user files by encrypting them and appending the .EByteLocker extension, effectively rendering these files inaccessible without a decryption key. As part of its attack strategy, EByte Locker modifies the desktop wallpaper to display a warning message, prompting the victim to seek further instructions within a text file named Decryption Instructions.txt. This file serves as the ransom note, informing the victim that their data has been securely encrypted and can only be decrypted by paying a specified ransom in cryptocurrency, with further contact instructions typically provided via an email address included in the note. This places victims in a precarious position where they must decide whether to comply with the ransomware creator's demands, with no guarantee of file recovery.
How to remove Anarchy Ransomware and decrypt _anarchy files
Anarchy Ransomware is a malicious software that encrypts files on infected systems, rendering them inaccessible to the user until a ransom is paid. Upon encrypting files, this ransomware appends them with the _anarchy file extension, which is a clear indicator of its presence. For example, a standard file such as
photo.jpg would be altered to photo.jpg_anarchy once encrypted by this malware. This type of ransomware typically uses strong cryptographic algorithms, which may include symmetric or asymmetric encryption, making it extremely difficult to decrypt the files without a unique decryption key. The ransomware's ransom note, a distressing message demanding payment for file retrieval, is displayed prominently using the command prompt message on the infected computer's screen. This message often instructs the victim on how to contact the cybercriminals, commonly through encrypted spaces like Telegram, providing further instructions on the payment process, usually in bitcoins. How to remove Clone Ransomware and decrypt .Clone files
Clone Ransomware is a malicious program that belongs to the infamous Dharma ransomware family, designed with the sole purpose of encrypting files on an infected system and extorting a ransom for their decryption. As a part of its functionality, this ransomware alters the filenames by adding a unique identifier, an email address of the attackers, and the new extension .Clone. This modification makes files like
document.txt turn into something like document.txt.id-12345.[attackeremail].Clone, rendering them inaccessible without the decryption key. Clone employs advanced symmetric or asymmetric cryptographic algorithms, which often makes decryption challenging without the specific decryption key possessed by cybercriminals. Consistent with other ransomware behaviors, Clone distributes ransom notes, which are mainly found as text files named clone_info.txt and as pop-up windows on infected devices. These notes contain minimalistic instructions urging victims to contact the attackers via specified email addresses to negotiate decryption. How to remove D0glun Ransomware and decrypt .@D0glun@[original_extension] files
D0glun Ransomware is a particularly menacing type of malware classified as ransomware, designed to encrypt the victim's files and hold them hostage in exchange for a ransom. This malicious software targets a wide spectrum of file types, including documents, images, and videos, disrupting personal and business operations. Upon infection, the ransomware appends a specific and distinct extension to the affected files following the pattern .@D0glun@[original_extension], visibly altering the filenames and rendering the files inaccessible. Its encryption algorithm is highly advanced, often utilizing a combination of symmetric and asymmetric cryptography, making decryption without the attacker’s involvement nearly impossible. Following the encryption process, victims are left with a pop-up window or altered desktop wallpaper displaying a ransom note, written in gibberish if the Chinese alphabet is not installed, informing them of the situation and directing them to pay a ransom in Bitcoin. This ransom note is strategically placed to ensure it is prominently seen, adding pressure to the victim's decision-making process.
How to remove BlackPanther Ransomware and decrypt .Bpant files
BlackPanther Ransomware is a malicious program recognized for encrypting user data and appending the .Bpant extension to files, effectively holding them hostage. This type of malware primarily targets sensitive and personal files, including documents, images, and databases, rendering them inaccessible without a cryptographic key. Upon infection, victims find a file originally named, for instance,
1.jpg transformed to 1.jpg.Bpant. The encryption employs robust cryptographic algorithms that are practically impossible to decrypt without the specific decryption key, typically known only to the cybercriminals behind the attack. Once encryption is complete, the ransomware alters the system's desktop wallpaper and presents a pre-login screen with a daunting ransom message. It also drops a text file, named Bpant_Help.txt, containing instructions on how victims can allegedly restore access to their files by making a cryptocurrency payment to an untraceable account. How to remove Hyena Ransomware and decrypt .hyena111 files
Hyena Ransomware is a pernicious form of malware that encrypts files on a victim's computer, rendering them inaccessible, and subsequently demands a ransom for their release. As part of the MedusaLocker family, this ransomware appends the .hyena111 extension to each affected file, making it unrecognizable to the system and unusable by the user. The attackers leverage advanced encryption methods, specifically RSA and AES algorithms, to secure the files in a way that prevents decryption without their unique decryption key. During the attack, READ_NOTE.html, a ransom note file, is deposited onto the compromised system. This file, often prominently displayed or found in multiple directories, informs victims of the breach, threatening to release, sell, or permanently lock data unless payment is received. In the note, victims are instructed not to use third-party software for file recovery, warning that attempts could result in data corruption.
How to remove WeRus Ransomware and decrypt .werus files
WeRus Ransomware is a malicious software program that targets user data by encrypting files and demanding a ransom for their decryption. This nefarious ransomware appends a .werus extension to the filenames of the encrypted files, which makes accessing the data without the decryption key impossible. For instance, a file named
document.docx would be renamed to document.docx.werus after encryption. The encryption mechanism employed by WeRus is robust, often involving sophisticated cryptographic algorithms that ensure only the attackers can provide the necessary decryption key. Once the encryption process is completed, WeRus changes the desktop wallpaper and drops a ransom note named Readme_[victim's_ID].txt across the victim's desktop environment. This note informs the victims of their encrypted files and demands a hefty payment, typically in Bitcoin, within a specific timeframe, warning that failure to comply might result in permanent data loss. How to remove Nnice Ransomware and decrypt .nnice files
Nnice Ransomware is a malicious software that targets individuals and organizations by encrypting files on their systems and demanding a ransom for decryption. This type of ransomware typically infiltrates through phishing emails with malicious attachments, compromised websites, or via unauthorized downloads from untrusted sources. Once it breaches a system, the ransomware encrypts files utilizing a sophisticated encryption algorithm, leaving them inaccessible to the user. Each affected file is appended with a .nnice extension, effectively rendering file types such as documents, images, and videos unusable without decryption. Victims are left with a stark reminder of the cybercriminal's presence: a ransom note. This note usually appears in a text file named read_me.txt, which is placed either in every folder containing encrypted files or prominently on the desktop. The note instructs victims on how to contact the attacker, often through an email address, and details the ransom payment method—typically involving cryptocurrencies to maintain anonymity.


















![How to remove D0glun Ransomware and decrypt .@D0glun@[original_extension] files](https://i0.wp.com/www.bugsfighter.com/wp-content/uploads/2025/01/d0glun-ransomware.webp?resize=324%2C235)






